What Equity, Respect, and Voice Mean to…
Cyproteck Technologies and CGD LLC Company history It all started in Corporate America… What Equity, Respect, and Voice Mean…

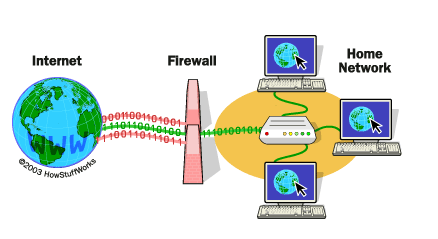
Firewalls have been a fundamental component of cybersecurity for decades, and they continue to play a critical role in protecting networks and data from unauthorized access. In this blog post, we’ll explore what firewalls are, how they work, and why they’re so important for cybersecurity.
What is a Firewall?
A firewall is a network security device that monitors and controls incoming and outgoing network traffic based on a set of predetermined security rules. Firewalls are designed to prevent unauthorized access to or from a private network while allowing legitimate traffic to pass through. They are typically deployed at the perimeter of a network, between the internet and an organization’s internal network.
How Do Firewalls Work?
Firewalls use a combination of hardware and software to enforce security policies and filter traffic. They are capable of examining the headers and contents of packets to determine whether to allow or block traffic based on a set of pre-configured rules. For example, a firewall might be configured to block all incoming traffic from a specific IP address or to only allow certain types of traffic, such as HTTP or HTTPS.
Firewalls can be configured to operate in several different ways, including stateful and stateless modes. Stateful firewalls maintain information about each connection passing through them, allowing them to make intelligent decisions about whether to allow or block traffic based on the state of the connection. Stateless firewalls, on the other hand, do not maintain this information, making them less effective at detecting and blocking certain types of attacks.
Why Are Firewalls Important for Cybersecurity?
Firewalls are a critical component of a comprehensive cybersecurity strategy for several reasons:
Conclusion
Firewalls are a critical component of a comprehensive cybersecurity strategy. They provide essential protection against unauthorized access, malware infections, and other types of cyber attacks. By deploying firewalls at the perimeter of a network and configuring them with the appropriate security policies, organizations can significantly improve their cybersecurity posture and reduce the risk of a data breach or other type of cyber incident.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Nunc sagittis mauris ac enim sagittis dignissim.
Cyproteck Technologies and CGD LLC Company history It all started in Corporate America… What Equity, Respect, and Voice Mean…
The main function of EDR is to provide continuous monitoring of endpoint devices to detect and respond to security incidents.
(Security Information and Event Management) Gives Security teams Enhanced Threat Detection

